Conventionally,a computer consists of at1.ast one processing element, typically a(73) and some form of memory.A.deviceB.CPUC.controllerD.network
题目
Conventionally,a computer consists of at1.ast one processing element, typically a(73) and some form of memory.
A.device
B.CPU
C.controller
D.network
相似考题
参考答案和解析
按照管理,一个计算机至少包括一个处理元素,典型的有CPU和某种形式的内存。
更多“Conventionally,a computer consists of at1.ast one processing element, typically a(73) and ”相关问题
-
第1题:
● One of the basic rules of computer security is to change your (73) regularly.
(73)
A. name
B. computer
C. device
D. password
正确答案:D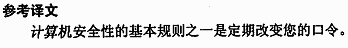
-
第2题:
Which of the following elements can be called the key element of a computer?(71)
A.printer
B.CPU
C.mouse
D.keyboard
正确答案:B
解析:A、C、D、是计算机的外设,不是基本元件。 -
第3题:
Tile hardware are the parts of computer itself including the(71)(CPU)and related microchips and micro -circuitry, keyboards, monitors, case and(72)(including floppy, hard, CD, DVD, optical, tape, etc...). Other extra parts called(73)or devices include mouse, printers,(74), scanners, digital cameras and cards(sound, colour, video)etc... Together they are often referred to as a(75)or PCs.
A.Central Processing Unit
B.Center Process Unit
C.Central Processing Unix
D.Counting Process Unit
正确答案:A
解析:CentralProcessing:中央处理器 -
第4题:
One of the basic rules of computer security is to change your(73)regularly.
A.name
B.computer
C.device
D.password
正确答案:D
解析:计算机安全性的基本规则之一是定期改变您的口令。 -
第5题:
Which element occurs first during the first-packet-path processing?()A. destination NAT
B. forwarding lookup
C. route lookup
D. SCREEN options
参考答案:D
-
第6题:
controls the operation of the computer and performs it's data processing functions.
A.CPU
B.Hard disk
C.Memory
D.Database system
正确答案:A
-
第7题:
IP multicasting is a set of technologies that enable efficient delivery of data to many locations on a network. Rather than making multiple copies of a message intended to be distributed to multiple recipients at the(71) of origin of a message, multicasting initially sends just one(72) and does not copy it to the individual recipients until it reaches the closest common point on the network, thereby(73) the bandwidth consumed. Network performance is significantly(74) because it isn't bogged down with the processing and transmission of several large data fries; each receiving computer doesn't have to(75) the transmitting server for the file.
A.point
B.bottom
C.head
D.sight
正确答案:A
-
第8题:
cloud storage is a model of computer of computer data storage in which the digital data is stored in logical pools.The physical storage spans multiple servers(somentimes in multiple locations),and the physical environment is typically owned and managed by a hosting company.As for the cloud concepet,the cloud storage service is one kind of( ).A.、laaS
B.PaaS
C.SaaS
D.DaaS答案:A解析: -
第9题:
Which element occurs first during the first-packet-path processing?()
- A、destination NAT
- B、forwarding lookup
- C、route lookup
- D、SCREEN options
正确答案:D -
第10题:
Your network consists of a single Active Directory forest. You have 50 portable computers and 50 desktopcomputers. All computers have 32-bit hardware. You plan to deploy Windows 7 and 10 corporateapplications to the computers by using a custom image. You need to prepare for the deployment by usingthe minimum amount of administrative effort. What should you do first?()
- A、On one computer, install Windows 7 and the corporate applications.
- B、On one portable computer and one desktop computer, install Windows 7 and the corporate applications.
- C、On a server, install and run the Microsoft Assessment and Planning (MAP) Toolkit.
- D、On a server, install the Windows Automated Installation Kit (AIK) and run Windows System ImageManager (Windows SIM).
正确答案:A -
第11题:
单选题You are the network administrator for ExamSheet. Your network consists of one Windows NT Server 4.0 domain and 35 Windows 2000 Professional computers. The network consists of five interconnected TCP/IP subnets. All of the computers use TCP/IP as the only network protocol. You are adding 15 Windows 2000 Professional computers to the network. You configure each of the new computers to use DHCP. The computers can communicate with each other but are unable to communicate outside their own subnet. You run the ipconfig command to examine the IP address on one of the new computers. The IP address is 169.254.101.72 You want to enable the Windows 2000 Professional computers to communicate outside their own subnet. What should you do?()AInstall a DHCP server.
BInstall a WINS server. Configure each computer to use WINS.
CCreate an Lmhost file on each computer.
DCreate a Hosts file on each computer.
正确答案: B解析: 暂无解析 -
第12题:
单选题The air distributor is conventionally driven by() and distributes into each cylinder by() certain sequence.Acamshaft;fresh air
Bcamshaft;starting air
Celectronic motor which is controlled by a computer;fresh air
Delectronic motor which is controlled by a computer;starting air
正确答案: D解析: 暂无解析 -
第13题:
Password is a(n)(71)series of characters that enables a user(72)a file, computer or program. On multi - user systems,(73)user must enter his or her password(74)the computer will respond to commands. The password helps ensure that unauthorized users do not access the computer. In addition, data files and programs may require a password.
Ideally, the password should be something(75)could guess. In practice, most people choose a password that is easy to remember, such as their name or their initials. This is one reason it is relatively easy to break into most computer system.
A.obvious
B.secret
C.important
D.easy
正确答案:B
-
第14题:
Calculator is(66) for performing arithmetic operations, but that requires human intervention to alter its stored program, if any, and to initiate each operation or sequence of operations. A calculator performs some of the functions of a computer, but usually operates only with frequent human intervention.Microcomputer's processing unit consists of one or more microprocessors, and includes storage and input-output(67). Personal computer primarily intended for(68) use by an individual.(69) computer can be hand-carried for use in more than one location. Minicomputer is functionally intermediate between a microcomputer and a mainframe. And supercomputer has the highest processing speeds available at a given time for(70) scientific and engineering problems.
A.suitable
B.well-formed
C.applicable
D.usable
正确答案:A
-
第15题:
● TCP/IP (71) layer protocols provide services to the application (72) running on a computer. The application layer does not define the application itself, but rather it defines (73) that applications need—like the ability to transfer a file in the case of HTTP. In short, the application layer provides an (74) between software running on a computer and the network itself. The TCP/IP application layer includes a relatively large number of protocols, with HTTP being only one of those. The TCP/IP (75) layer consists of two main protocol options—the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP).
 正确答案:A,B,A,C,D
正确答案:A,B,A,C,D
-
第16题:
Although the bulk of industry resources and energies have focused on developing the fastest(71)or slickest(72)more and more mindshare is turning to the evolution of the computer interface. Advancements in the areas of input devices,(73)processing and vitual reality could lead to fundamental changes in the way human and computer interact. The technological battlefield of the future will be adding layers between the user and the raw machine to make the(74)as invisible as possible.(75)represents the next evolutionary step for the interface.
A.microprocessor
B.format
C.structure
D.procedure
正确答案:A
-
第17题:
is one kind of software absolutely necessary for every computer.
A.Operating System
B.Word processing
C.Keyboard
D.Center Processing Unit
正确答案:A
解析:译文:操作系统是计算机运行不可缺少的一类软件。 -
第18题:
For many years, the principle goal of computer(73)was to write short pieces of code that would execute quickly. The(74)needed to be small, because memory was expensive, and it needed to be fast, because processing power was also expensive.
A.users
B.programmers
C.that
D.program
正确答案:B
解析:题意为“计算机程序员编写代码”,所以答案为B。 -
第19题:
( )is the key element for the whole society.
A.Keyboard B.Information C.CPU D.Computer
正确答案:B
-
第20题:
True patriotism consists( )putting the interests of one country above everything,including one’s life.
in答案:解析:consist in“在于,存在于”;consist of“由……组成” -
第21题:
The network at Company Ltd. consists of one Windows NT Server 4.0 domain and 35 Windows 2000Professional computers. The Company network consists of five interconnected TCP/IP subnets. All of thecomputers use TCP/IP as the only network protocol.You are adding 15 Windows 2000 Professional computers to the network. You want to enable theWindows 2000 Professional computers to resolve NetBIOS names to TCP/IP addresses.What should you do? ()
- A、Install a DHCP server. Configure each computer to use DHCP.
- B、Install a WINS server. Configure each computer to use WINS.
- C、Create a Lmhosts.sam file on each computer. Add an entry containing the TCP/IP address and NetBIOS name for each computer on the network.
- D、Create a Hosts.sam file on each computer. Add an entry containing the TCP/IP address and NetBIOS name for each computer on the network.
正确答案:B -
第22题:
You are the network administrator for your company. The network consists of a single Active Directory domain. The domain includes an organizational unit (OU) named Processing. There are 100 computer accounts in the Processing OU. You create a Group Policy object (GPO) named NetworkSecurity and link it to the domain. You configure NetworkSecurity to enable security settings through the Computer Configuration section of the Group Policy settings. You need to ensure that NetworkSecurity will apply only to the computers in the Processing OU. You need to minimize the number of GPO links. What should you do?()
- A、 Link NetworkSecurity to the Processing OU. Disable the User Configuration section of NetworkSecurity.
- B、 Link NetworkSecurity to the Processing OU. Remove the link from NetworkSecurity to the domain.
- C、 Modify the discretionary access control list (DACL) for NetworkSecurity to assign all computer accounts in the Processing OU the Allow - Read and the Allow - Apply Group Policy permissions.
- D、 Modify the discretionary access control list (DACL) for NetworkSecurity to assign the Authenticated Users group the Deny - Apply Group Policy permission and to assign all of the computer accounts in the Processing OU the Allow - Read and the Allow - Apply Group Policy permissions.
正确答案:B -
第23题:
单选题You are the network administrator for your company. The network consists of a single Active Directory domain. The domain includes an organizational unit (OU) named Processing. There are 100 computer accounts in the Processing OU. You create a Group Policy object (GPO) named NetworkSecurity and link it to the domain. You configure NetworkSecurity to enable security settings through the Computer Configuration section of the Group Policy settings. You need to ensure that NetworkSecurity will apply only to the computers in the Processing OU. You need to minimize the number of GPO links. What should you do?()ALink NetworkSecurity to the Processing OU. Disable the User Configuration section of NetworkSecurity.
BLink NetworkSecurity to the Processing OU. Remove the link from NetworkSecurity to the domain.
CModify the discretionary access control list (DACL) for NetworkSecurity to assign all computer accounts in the Processing OU the Allow - Read and the Allow - Apply Group Policy permissions.
DModify the discretionary access control list (DACL) for NetworkSecurity to assign the Authenticated Users group the Deny - Apply Group Policy permission and to assign all of the computer accounts in the Processing OU the Allow - Read and the Allow - Apply Group Policy permissions.
正确答案: B解析: 暂无解析
